These days capitalism and democracy seem to mean that it’s never too early to take advantage of the misery of others, and the outbreak of the novel coronavirus, COVID-19, is the latest proof point.
On Saturday the Washington Post reported that an agency within the State Department had compiled a report of two million tweets, which peddled conspiracy theories about the COVID-19 coronavirus outbreak.
Among the hoaxes compiled in the report and reported by the Post included the suggestion that the virus had been created by the Bill and Melinda Gates Foundation or was the result of a bioweapon developed by the Chinese government.
In all, these tweets represent about 7 percent of the total tweets surveyed by the government, according to the Post’s reporting.
Critically, the report indicated that some of the misinformation spread online appeared to be the result of “inauthentic and coordinated activity,” the Post reported the document saying.
The report mirrors warnings from cybersecurity firms like Check Point Software, which issued a report tracking the launch of new websites linked to themes around the coronavirus outbreak earlier this month.
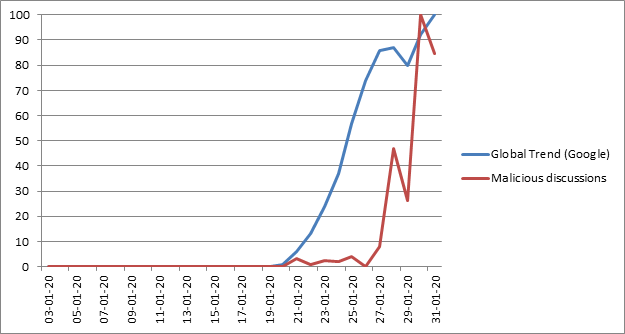
According to the company’s Global Threat Index for January 2020, “cyber-criminals are exploiting interest in the global epidemic to spread malicious activity, with several spam campaigns relating to the outbreak of the virus.”
The company correlated Google search terms with what it deemed to be “malicious discussions” about the virus, and showed them to be tightly correlated.
In one instance, a hacking campaign targeting web users in Japan distributed malicious email attachments by pretending to be a Japanese disability welfare service provider. The email provided misinformation about the spread of the coronavirus in several Japanese cities, and when a user opened an attachment to the email, they downloaded a modular, self-propagating Trojan virus onto their computer.
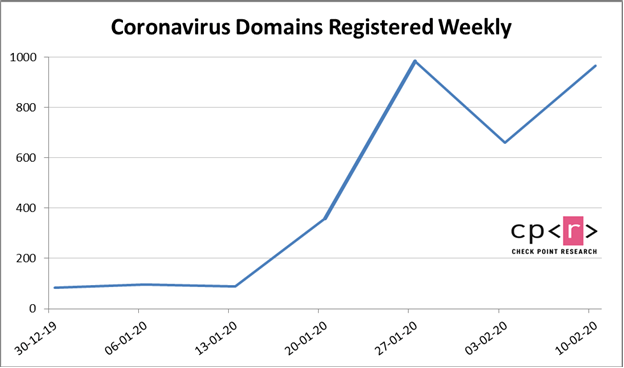
Email campaigns represent one threat, but another one that the security firm tracked was new websites with domain names linked to the virus.
The company already spotted one fake website, “vaccinecovid-19.com”. It was first created on February 11, 2020 and registered in Russia. According to Check Point, “the website is insecure, and offers to sell ‘the best and fastest test for Coronavirus detection at the fantastic price of 19,000 Russian rubles (about US$300)’.
Facebook, Amazon, and Twitter have all taken steps to remove misinformation about the novel coronavirus from their platforms including advertisements offering purported cures for the disease.
Earlier this month, the big tech companies met with representatives of the World Health Organization to come up with a plan and coordinate on ways to combat misinformation and scams online.
Earlier this week, Facebook issued the following statement about its continuing response to misinformation campaigns on the site:
As world health officials issue new guidance and warnings about coronavirus (COVID-19), we’re continuing our work to connect people to information from regional and local health organizations and limit the spread of misinformation and harmful content about the virus.
Connecting People to Accurate Information and Helpful Resources
Anyone who searches for information related to the virus on Facebook is shown educational pop-ups on top of search results connecting them to expert health organizations including the World Health Organization (WHO). We’ve launched these globally over the last few weeks in all languages on Facebook, directing people to the WHO. In several countries we are directing people to their local ministry of health. For example, in the US we are directing people to information from the Centers for Disease Control and Prevention (CDC) and in Singapore, we’re directing people to the Singapore Ministry of Health. Moreover, in countries where the WHO has reported person-to-person transmission and deaths, we’ve shown additional messages to people toward the top of News Feed with more information.
from TechCrunch https://ift.tt/39hT5uI
Comments
Post a Comment